Authentication, access control cryptography¶
1. Authentication¶
Identification who you are. e.g. email or username Authentication proof that you are who you say you are. e.g. password or OAuth token. e.g. password or OAuth token.
Authentication mechanisms used to confirm a users identity: - The user knows something. A password, pin, handshake, security question. - The user has something. A bank card, an id card, an RFID tag. - The user is something. Biometrics, fingerprints, retina, face scan, voice pattern.
1.1. Passwords - something you know¶
Disadvantages: - Use - can be tedious to use for every authentication. - Disclosure - sharing the password allows unauthorized users to access the object. Changing the password then inconveniences all other authorized users. - Revocation - to revoke access, the password must be changed and not shared with the user. Same problem with other authorized users. - Loss - passwords can be easily forgotten.
Hackers try to guess passwords. All passwords can be guessed.
Password storage - Systems store username-password combinations in a table like fashion. - The password is stored in an encrypted way. - Often a part of the username is included in the encryption to enforce unique hashes. This is called added salt to the encryption (something that is not a part of the password)
Password alternates (things you know). - Patterns - Security questions - Puzzles - etc.
Attacking passwords: - Dictionary attack - use of a premade list of common passwords - Using a rainbow table - similar to dictionary attack but with an encrypted table (and the decrypted pair) - Inferring a password - using information you know about someone to guess their password (you know their childs name/dogs name/date of birth) - Guessing probable passwords - using statistics of human psychology - Defeating concealment - uncovering a stored password - Exhaustive attacks - brute force, every combination
1.2. Biometrics - something you are¶
Biometrics are based on the physical characteristics of the body e.g. fingerprint, hand geometry, retina/iris, voice, handwriting, signature, typing characteristics, blood vessels in finger/hand, face, facial features
Advantages: - Cannot be lost. - Does not need to be remembered. - Difficult to be forged. - Always on hand.
Disadvantages: - Relatively new. Can be considered invasive. - The devices are expensive. - Single point of failure. If the fingerprint scanner fails due to a sore or something else, what do you do. - Every biometric reading is different and thus the formulae have to take into account variation. Thus a threshold for acceptance is established, accepting "close enough" biometrics. This can lead to false positives (accepting when you should not) and false negatives (rejecting when you should not).
| Is the correct person | Is not the correct person | |
|---|---|---|
| Test is positive | True positive = a | False positive = b |
| Test is negative | False negative = c | True negative = d |
| Sensitivity = a / (a+c) | ||
| - the ratio of correctly accepted matches amongst the accepted tests. | ||
| Specificity = d / (b+d) | ||
| - the ratio of the correctly denied matches amongst the denied test. |
Increasing sensitivity will decrease specificity. I.e. if you want to get more true positives you will get more false negatives. The system will be stricter. And visa/versa.
Accuracy or efficacy = (a + d) / (a + b + c + d) - the ratio of true matches amongst all tests. Prevalence = (a + c ) / (a + b + c + d) - the ratio of acceptance matches amongst all tests.
Identification vs authentication with biometrics. - Identification using a fingerprint would mean running through all fingerprints to find a matching one. - Authentication using a fingerprint would mean testing the fingerprint against a saved fingerprint. - Biometrics is advanced enough to do authentication, but success and failure rates are still too loose to use it for identification.
1.3. Tokens - something you have¶
Tokens are physical/electronic objects that can be used to authenticate a user. - Keys - Access card - Passport - Cookies in the browser - OAuth tokens
There are two kinds of ways tokens interact with readers: - Active - tokens that interact with the reader in some way either by being a part of the communication or allowing their state to be changed by the reader. - Passive - these tokens to nothing. They just have values that are read.
There are two kinds of states saved in tokens: - Dynamic - think of Google 2FA. The password is unique on each entry. - Static - static tokens values never change.
2. Access control¶
Federated identity management - unifies the identification and authentication process of a group of systems. A user can use the individual systems without having to be reauthenticated. Single-sign-on - takes over sign-on an authentication to several independent systems for a user. When a user moves to another system, they are authenticated by the SSO. Multifactor authentication - using more than one authentication technique.
Subject - the person or program wanting to gain access. Object - the file, table, program, database, hardware, network connection etc that a subject wants to gain access to use/modify. Access mode - read, write, modify, delete, execute, create, destroy, copy, export, import, etc. Access policies - a list of rules saying which subjects have which access modes to which objects.
Access policies¶
These should not be made on an adhoc basis as things are needed. A higher-level security policy should be governing the access policies.
Implementation goals: - Check every access - access is not permanent and can be revoked. - Enforce least privelege - give users the least amount of access that they can do their jobs with. - Verify acceptable usage - sometimes write access must be done in a certain way.
A reference monitor - access control must always be invoked, tamper proof and verifiable.
| Control type | Short Desc |
|---|---|
| Access control directory | A directory per user per file with the access rights |
| Access control matrix | A single matrix of users and files with access rights at the intersection |
| Access control list | A combination of the above. A directory of files, each file points to a list of user access matrices. |
3. Cryptography¶
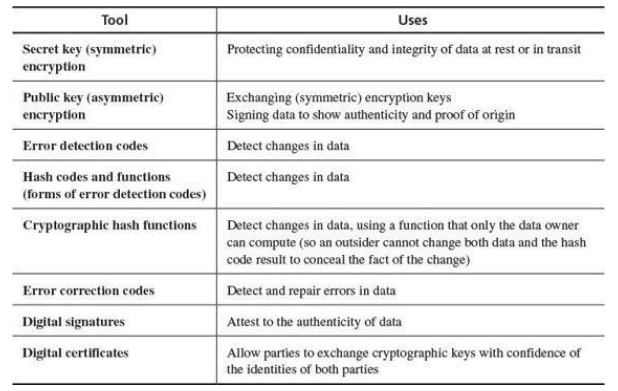
Encryption - converting plaintext into cypher text. Decryption - converting cypher text into plain text. Algorithm - the steps used to do the encryption/decryption Key - a device used in the algorithm so that the cypher text is dependant on this key.
Substitution cipher - replacing one character with another Transposition cipher - mixing up the positions of the plaintext
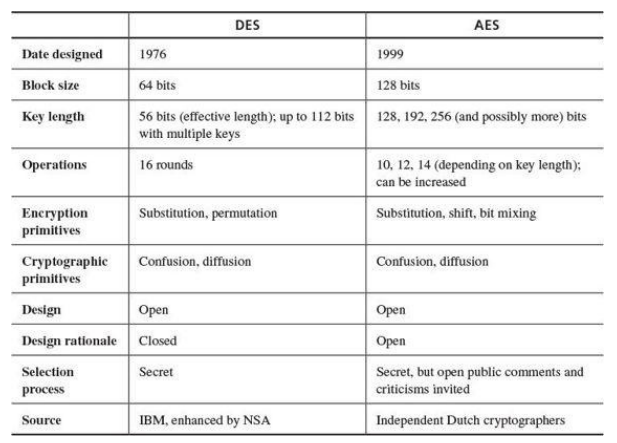
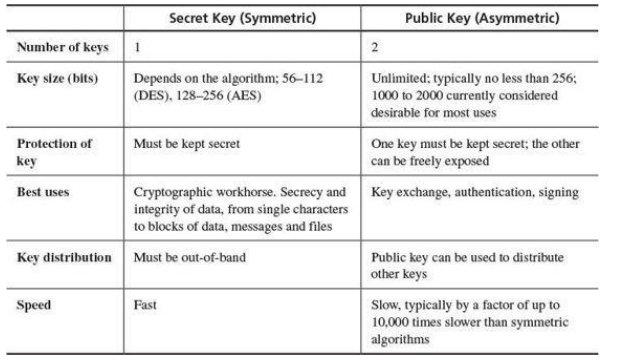
Symmetric encryption - encryption and decryption use the same key Asymmetric encryption - there is a key to encrypt and a key to decrypt
Cryptographer - the person who uses encryption to conceal messages. Cryptanalyst - a person who studies encryption and encrypted messages in the hopes to find the hidden messages.
Work factor - the difficulty required to break the encryption.
Key distribution issue - how to get an assymetric key to another user in secret. Key management issue - how to keep keys safe.
Stream cypher - encryption of data one bit/byte at a time. - speed of transformation - there is no need to buffer data into chunks, as it is read it can be encrypted. - Low error propagation - an error in encryption only effects that character. - Susceptable to insertions/modifications - Low diffusion - all the cypher information is contained in the one symbol. Block cypher - encryption of data in 64/128/256 chunks. - High diffusion - all the cypher information is split accross the block. - Immunity to insertion - Slow to encrypt - Padding is required for unfilled blocks. - Prone to error propagation.
Examples of symmetric encryption schemes:
Asymmetric encryption scheme RSA: - Uses the difficult factorisation problem which has been unbroken for years. - Two keys are provided A and B. Either can be used for public/private keys. - Messages encrypted with A can be decrypted with B and visa versa.
To send a message from one user to another: - Person 1 encrypts the message with person 2's public key and sends the message to person 2. The application of the public key again will not decrypt the message. Only person 2's private key will decrypt the message.
Encoding/decoding for transmission: - This involves error detection which is different to encryption decryption. - Parity bits - Hash sums
Sometimes this information needs to be encrypted so that a man-in-the-middle cannot change this information enroute.
SHS/SHA (secure hash standard/algorithm) MD4, MD5 - an encrypted form of a hashsum and can determine if a file has changed.
Digital signatures - use asymmetric encryption to determine that only person A could have sent this. - Digital signature must be non-predutiatory (i.e. it must be provable that person A sent the message) - this is ensured by RSA - They must be authentic (unforgeable) - this is ensured by RSA - They must not be alterable (cannot be changed by an interceptor) - this is ensured by SHS or SHA. - They must not be reuseable (must be attached to the document) - this is ensured by RSA/SHA.
The commutativity of RSA allows for the creation of signatures. - This means that a message can be encrypted with either the public or private key. But must be decrypted by the other key. - Person A can then encrypt a message with their private key that can then be decrypted by their public key. This is backwards to the normal encryption/decryption since anyone can decrypt it, but ONLY A could have encrypted it. I.e. a signature.
Thus to send a message M which is signed from person A to person B the following steps are taken: 1. Message M (with its hash) is encrypted with A's private key. (Ensuring authenticity and unalterability and unreusability). 2. The encrypted message then passes a second round of encryption with person B's public key. (Ensuring secrecy). 3. To decrypt person B will then do the first round of decryption with their private key (only they can do this since it was encrypted with their private key) uncovering an encrypted message. 4. They then do a second round of decryption using A's public key (anyone can do this since the key is public). 5. They will then have access to the original message M including the hash.
Establishing trust:
Certificate Authority¶
- A certificate is an identify-public key combination signed by a certificate authority.
- Any person can imitate a bank or website and sign the website with their private key and post their public key. How do you know that the public key belongs to that bank?
- In reality we can trust that person A works in our company and can be trusted because our boss can go up the heirachy and ask for their boss to confirm person A's identity.
- A certificate authority acts as the "boss" of the internet.
